How to Download Naruto Senki OverCrazy V2 Mod Apk Final – In this modern era, everything can be done more easily. Almost all daily activities can be completed with the help of a smartphone.

Table of Contents
How to Download Naruto Senki OverCrazy V2 Mod Apk Final Character 2024
Smartphones circulating today are indeed very diverse, and must already have specifications that are quite above average.
Read more:
- Download Naruto Ultimate Ninja Storm 4 PPSSPP
- Download The Latest 60+ Naruto Senki Mod apk game
- Download Naruto X Boruto Ninja Voltage Mod Apk game
- Gogo Live Mod Apk Latest Unlimited Coin & VIP Apk
By using smartphones we can easily get an exciting gaming experience. if want to download Naruto Senki OverCrazy? then follow this guide:
In fact, we don’t need to pay extra to buy a Playstation or other game console at a relatively expensive price and large size.
If it’s just to fill spare time so you don’t get bored, we can use the smartphone we use to play games.
The choice of games for Android smartphones is currently very diverse, ranging from car racing games, action, fantasy, battle royal, MOBA, and the most exciting is games adapted from anime series like Naruto.
If you are a fan of the Naruto anime, you will definitely like to play the game that I will discuss this time, namely Naruto Senki Over Crazy Full Character Mod Apk.
The Naruto game that I share is a game that has been modified in such a way or better known as the mod apk.
In the Naruto Senki Over Crazy mod apk, many features have been modified, so that it will make it easier for us to play it.
The features that have been in the mod include unlimited money, all characters are open, and are exactly the same as those in the Naruto anime. So we don’t need to buy them anymore.
Apart from the many features that are already open, the file size of Naruto Senki is also very small, only 68 MB. So it is very light to play on a potato cellphone though.

Download Naruto Senki Mod Apk Full Character No Cooldown Skill
| Game Name | Naruto Senki Overcrazy V2 Mod Apk |
| Version | Mod Apk |
| Game Size | 68 MB |
| Mod By | Riicky Ahmad Fauzi |
| Update | Ultimate Ninja Storm 4 narcissus |
How to Install
To be able to play games smoothly on an Android smartphone, you should follow the following installation steps:
- Make sure you download the Naruto Senky Over Crazy 2 game file from the download link on this site.
- Then open the Naruto Senky Over Crazy 2 Mod APK file, and install it.
- Wait until the installation process is complete.
- When it’s finished, open it and play the Naruto Senki game over crazy full character.
Apart from this Naruto game, you can also play Naruto X Boruto Ninja Voltage which is no less exciting.
Naruto Senky Over Crazy V2 features
- There is no delay.
- An unlimited number of coins and money (Unlimited Coin & Money).
- Madara’s voice was changed to Suigetsu’s voice.
- Not a Blood Mod like before.
- Mod Results from Riicky Ahmad Fauzi.
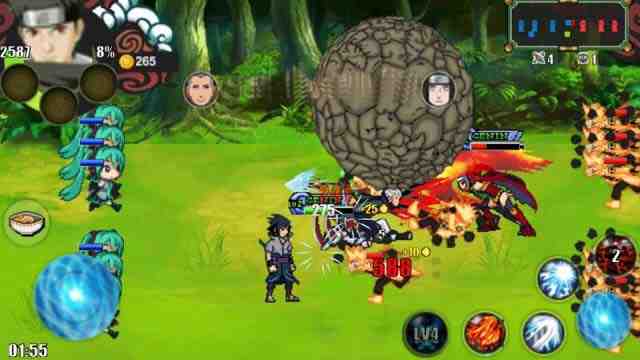
Naruto Senki Over Crazy has several game modes that you can play. In Battle mode, each character has 3 moves that can be used to fight and attack enemies.
Apart from that, there are also special moves that you can get by buying in the skill menu and character selection.
If you already use the Naruto Senki beta mod apk, you don’t need to spend more money to buy it because all items that are locked are already unlocked.
Then there is the battle mode, where there will be 2 different teams that beat each other and destroy the towers in the opponent’s territory. This mode is almost like the Moba game.
The characters you use will be accompanied by 2 supporting characters randomly selected by the computer.
Apart from that, there are also frog fighters. This also applies to the opposing team.
There are many more games adapted from the Naruto anime series, for example, Naruto Ninja Impact which was previously for PC but is now designed to be played on an Android smartphone.
The open-source Android operating system is indeed very beneficial for users and developers.
Because it allows people who have programming skills to develop games and applications for Android.
This has indeed been proven with great discoveries, for example, the PS 2 and PSP games can now be played on Android phones with the help of an emulator.
Disclaimer: All forms of download files on the Technadvice.com site are just for educational purposes only.
DMCA: Technadvice.com complies with 17 U.S.C. * 512 and the Digital Millennium Copyright Act (DMCA). It is our policy to respond to any infringement notices and take appropriate action. If your copyrighted material has been posted on the site and you want this material removed, Contact us.
Conclusion:
So, friends, that’s above on how to download Naruto Senki OverCrazy V2 Mod Apk, If you want to play this game, but don’t know the download link, then you can request us via the comments column or contact us.
Don’t forget to bookmark and always visit every day Technadvice.com because here you can find the latest technology information such as How-to Guide Tips and Tricks Blogging Digital Marketing Windows Android Root Social Media games, ETC. Best of luck.






![6 Easy Ways to Fix Word Not Responding on Windows 10 [2024] 6 Easy Ways to Fix Word Not Responding on Windows 10](https://technadvice.com/wp-content/uploads/2023/03/6-Easy-Ways-to-Fix-Word-Not-Responding-on-Windows-10-100x70.png)






Naruto dhippudin